Technology
Blockchain Technology 101
Powered by blockchain
Authentys uses SHA 256 hash to securely store the document in the cloud and the user will be able to send access tokens to others. Tokens can set time limits/uses/expiration for that person to view the document.
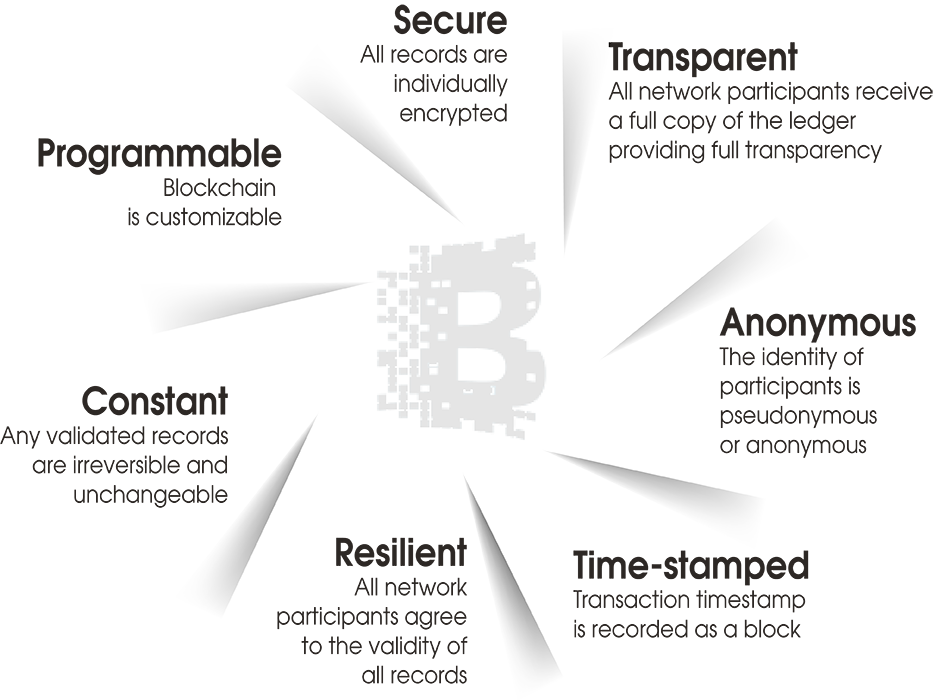
Value drivers of Digital Ledger Technologies
The future is decentralization
The expansion of the gig economy
Decentralization of nearly every sector from information to labor to energy
Law of economics: Reduces costs, improves service
Hyper-localizes transactions and, in turn, power
Why decentralization matters
Eliminates the need for payment processors
Transfers power and control from large entities to a broader network
Reduces transaction cost
No one entity holds the data

The self-sovereign life
The cryptocosm created by joining blockchain technology to cryptography is powerful. Its core architecture makes security a property of the system––not an afterthought.
Allowing people to control their own identities and their own security––rather than relying on an unvested third party––shifts power to the user.
The Future
Decentralized Digital Identity
Authentys is currently in discussions with Microsoft to incorporate a digital identity platform into the Authentys solution.
As the DID technology advances, Authentys will incorporate decentralized identity, biometrics, verifiable credentials, identity hubs and zero-knowledge proofs.

Decentralized Identifiers (DIDs)
Are a new type of identifier for verifiable, "self-sovereign" digital identity that reside on a blockchain.
Allows users to create unique digital identities that they personally own and control – independent from any centralized registry, identity provider, or certificate authority.
Eliminate the need for users to create any user id and password, eliminating the hacking issue.
Are linked to decentralized public keys and paired with the user’s encrypted personal datastores.
Do not use any personally identifiable information (PII) as part of the DID.
Provide a secure, anonymous, private, portable and non-correlatable digital identity for users.

